TOTAL SECURITY SOLUTION
SOLUTION
Combination of Biometrics and
RFID in a security solution
Combination of
Biometrics and
RFID in a security solution
Biometrics and RFID in security solutions have many complementary aspects,
so they can complement each other’s strengths and weaknesses,
and in harmony with other solutions as well as security solutions.
It has many advantages in building an integrated solution.
Examples of that are as follows.
Biometrics and RFID in security solutions have many
complementary aspects, so they can complement
each other’s strengths and weaknesses, and in
harmony with other solutions as well as security solutions.
It has many advantages in building an integrated solution. Examples of that are as follows.
Access control system
Time Attendance system
Mean depts system
Vehicle management system
Interworking with other exhibition systems
OUT LINE
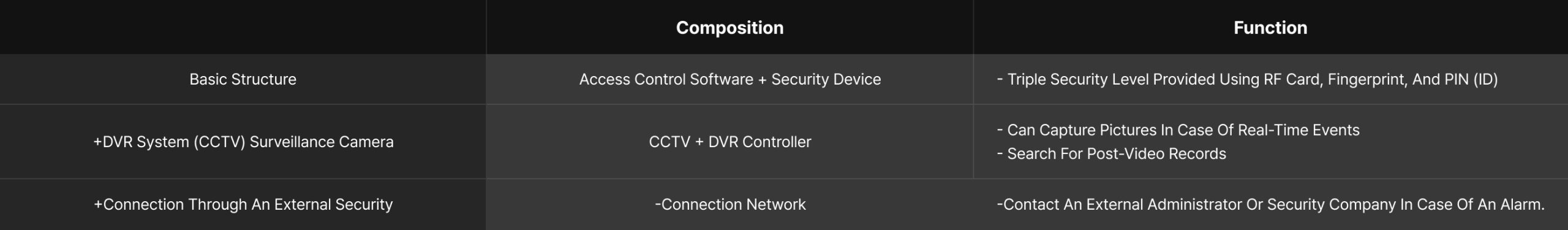
Existing security systems using keys or passwords will make security very ineffective. However, using fingerprint recognition and RF cards, access control systems can provide a different level of security. The access control system is a system developed to operate locks on doors and identify visitors, and RF Readers placed at each designated point read the ID of the access card and send it directly to the computer through serial communication or LAN to determine whether the card holder is allowed. And depending on the result, the Door Controller or other device may be controlled through the controller. Communication and control are also possible from a long distance through the Internet.
Existing security systems using keys or passwords will make security very ineffective.
However, using fingerprint recognition and RF cards,
access control systems can provide a different level of security.
The access control system is a system developed to operate locks on doors and identify visitors, and RF
Readers placed at each designated point read the ID
of the access card and send it directly to the
computer through serial communication or LAN to determine whether the card holder is allowed.
And depending on the result, the Door Controller or
other device may be controlled through the
controller. Communication and control are also possible from a long distance through the Internet.