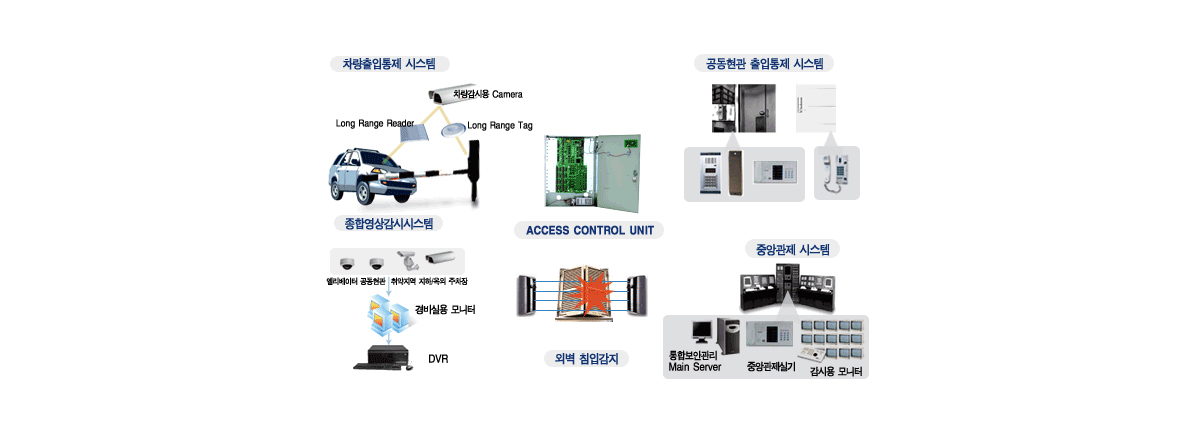
-

-
BIOMETRICS & RFID
TOTAL SECURITY SYSTEM PART
-
PRODUCTS
SEARCH PRODUCTS
-
CONTACT
TEL : 82-31-446-5388 / 82-31-447-5388
FAX : 82-31-448-5388
E-MAIL : kk5388@ekjtech.co.kr

Please take a QR CODE by smart phone,
we will show the map by google map.